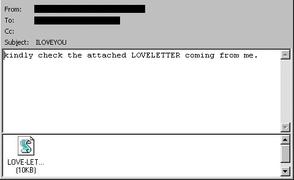
In May of 2000, a young hacker in the Philippines named Onel de Guzman created an email worm that would change the way the world thought about cybersecurity. De Guzman had just dropped out of college after his professors rejected his undergraduate thesis paper, on the possibility of using malware to steal internet passwords from people in the neighborhoods nearby. He wanted everyone to have internet access, which he believed to be necessary in order to access the sum of humanity’s knowledge and improve one’s quality of life; he even called it a human right. It was clear that de Guzman had been experimenting with a functional version of such a program for some time. When his professors rejected the thesis for being unethical and likely illegal, de Guzman left, calling the professors close-minded.
After leaving school, de Guzman planned to continue with his goal of using the script he had created to steal internet passwords from the people in his neighborhood. Out of curiosity, he removed the restrictions on spread and location while tinkering with it one night. As a test, he sent it to one person in Singapore he had met in a chat room before heading out with friends. When he returned, international news outlets were discussing a global manhunt for the hacker who had crippled global infrastructure with malware for which the naïve online world was not yet ready. Within 24 hours, de Guzman’s experiment had infected around 45 million Windows computers, and ultimately infected around 10% of the world’s internet-connected computers before being mitigated, a process that cost billions of dollars in addition to the repairs and lost productivity. The United States Congress launched investigative hearings after major corporations as well as government institutions were crippled: the Pentagon, as well as the British Parliament and MI6, shut down their own email systems out of fear that the hacker was attempting to steal critical information from their servers. Funnily enough, the script was meant to send passwords stored on the computer to an email address de Guzman had created, but that section of the script was incomplete, and the sheer number of infections caused the web server hosting the email to shut down, making the worm essentially useless for doing anything but replicating itself and causing chaos.
Soon, the Philippines National Bureau of Investigation appeared at de Guzman’s doorstep. They had received a tip that the hacker had attached a signature and email to his script, which they eventually tracked back to his family’s home. De Guzman’s mother, fearing prison time for her son, hid his computer, but the police found floppy disks Guzman had hidden in his room which contained copies of the worm, confirming that it was his creation. De Guzman later confirmed that he had written the script in court. However, the police needed to prove that de Guzman had intended to cause the mayhem and destruction that had resulted from his test, and all they were able to get out of him was that “it was possible” that he had released the virus accidentally. The ensuing trial found that he had broken no law, as he did not steal physical property nor did he violate the only computer-related crime on the books, which was credit card fraud. The Philippines, like much of the developing world, had barely considered the possibility of a person committing crimes using nothing but a computer and an internet connection. Soon after, the Philippines passed a law banning creation of malware and hacking, but it was too late to try de Guzman. Speaking with an interviewer in 2020 for the first time since the incident, de Guzman said he regretted sending the virus and causing so much chaos. Shy by nature, he hid from the publicity that surrounded his creation and the ensuing infamy and praise in hacker circles (although much to the chagrin of world leaders, many hacker communities stated that it would be trivial to outdo de Guzman’s creation).
De Guzman’s worm, barely more than an experiment that rapidly spiraled out of control, shocked global leaders and tech companies into doing something about cybersecurity, a task that was often seen as a waste of time and money. The United States Senate hearing on the Love Bug described it as “the equivalent of a nuclear bomb going off in cyberspace” and they repeated what the financial services industry had told them: if the bug had written over spreadsheets instead of just text and images, the financial services industry would have essentially collapsed overnight. They also discussed newer worms that used exploits in different email systems that automatically opened links embedded in emails, which meant that even without the user clicking on an attachment the worm could overtake their computer immediately after the email was received. They discussed how the Department of Defense had been completely unprepared for the worm, and that hundreds of employees opened the attachment. In general, they found that even the United States wasn’t ready for a new age of malware and hacking, and that the developing world was entirely unprotected. The worm’s reign of terror may have lasted less than a week, but it filled the world with such a fear of the potential that hacking could have in the future that corporations, nations, and users around the globe began learning ways to protect themselves from hacking attempts. It was made clear that just because this time it was a student in the Philippines testing his code, next time it could be something far more malicious.
https://babel.hathitrust.org/cgi/pt?id=pst.000047033856&view=1up&seq=14 – Senate Committee on Financial Services hearing on the ILOVEYOU “virus”
https://www.bbc.com/news/technology-52458765 – an interview with de Guzman
About the Author
After working as an intern at CMoA during the summer of 2021, Ben Schmidt joined the team part-time while working on his capstone project at Georgia State University, with a plan to continue to full-time when he graduates in May. With a background in Public History, Ben has worked in and with archives, museums, and historic preservation organizations in a variety of different positions, ranging from exhibit creation to public advocacy to tour planning, but his interest primarily lies in collections and archives. He is finishing a Master’s in Heritage Preservation at GSU and has a Bachelor’s in History with a minor in Public History from Kennesaw State University. He also loves computers and history, making the museum a great fit for his interests.





